Next Generation SIEM
Our cloud SIEM service provides centralized security monitoring for your cloud, on-premises, or hybrid environments, covering your endpoints, network, syslog, and cloud instances.
Next Generation SIEM
Our cloud SIEM service provides centralized security monitoring for your cloud, on-premises, or hybrid environments, covering your endpoints, network, syslog, and cloud instances.

Next Generation SIEM
Our cloud SIEM service provides centralized security monitoring for your cloud, on-premises, or hybrid environments, covering your endpoints, network, syslog, and cloud instances.
Next Generation SIEM
Our cloud SIEM service provides centralized security monitoring for your cloud, on-premises, or hybrid environments, covering your endpoints, network, syslog, and cloud instances.

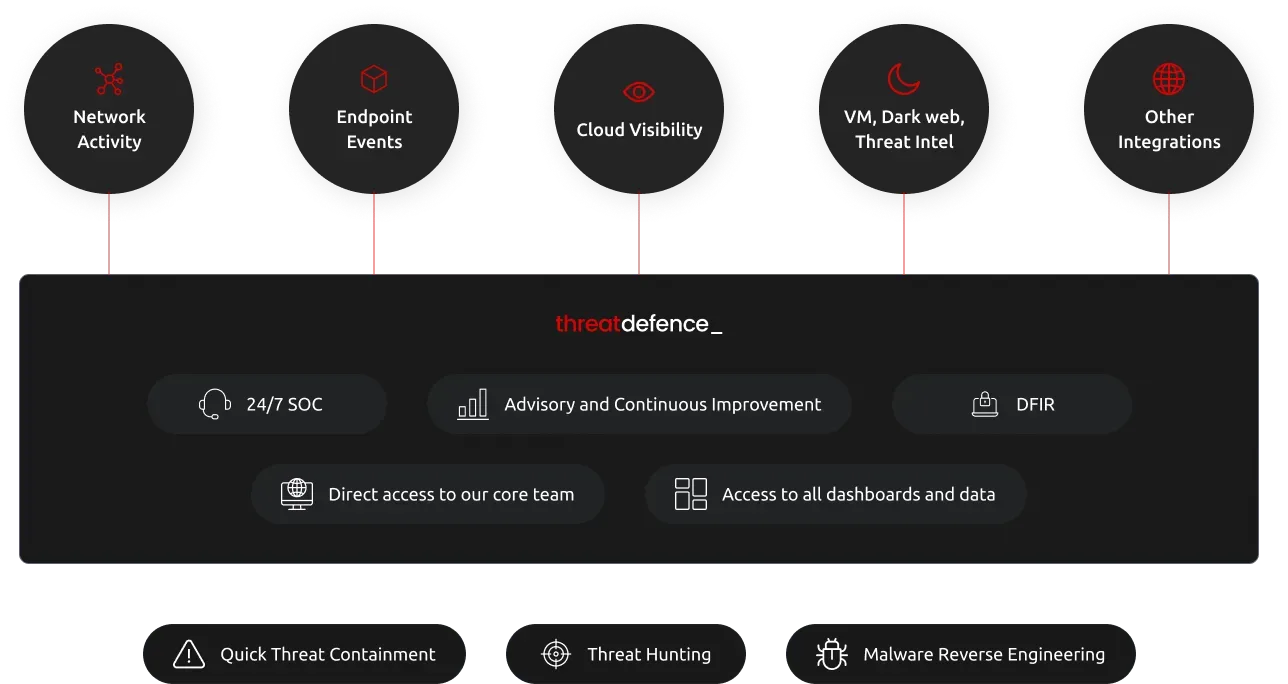
Foundation for Evidence-Based Security Operations
Foundation for Evidence-Based Security Operations
Integration Guarantee
We want your data to work for you - we guarantee that we can ingest data from your environment, would it be an enterprise system or a bespoke application.Integrated AI
Virtual AI assistant, automation tools, intelligent correlations and machine learning detections helping you to response to threats in minutes.SecOps Tools
End-to-end SecOps toolset, including vulnerability management, deception, NDR, cloud visibility and many other features.Deploy Anywhere
Our SIEM platform can be used either as a cloud service or deployed on-premises, whether it's in your own data center or public cloud instance.
Integration Guarantee
We want your data to work for you - we guarantee that we can ingest data from your environment, would it be an enterprise system or a bespoke application.Integrated AI
Virtual AI assistant, automation tools, intelligent correlations and machine learning detections helping you to response to threats in minutes.SecOps Tools
End-to-end SecOps toolset, including vulnerability management, deception, NDR, cloud visibility and many other features.Deploy Anywhere
Our SIEM platform can be used either as a cloud service or deployed on-premises, whether it's in your own data center or public cloud instance.
Streamline Your Operations with Our Cloud Platform
Delivered as a fully managed cloud service, our platform can be operational in minutes, saving time, resources, and overall cost of ownership. There is no learning curve as you do not need to configure or manage the platform.


Enterprise-Grade Capabilities
Our cloud SIEM supports numerous integrations, including syslog, cloud platforms, API connectors, network sensors, external data and more.
Enterprise-Grade Capabilities
Our cloud SIEM supports numerous integrations, including syslog, cloud platforms, API connectors, network sensors, external data and more.
- Role-based Access Control
- Log Storage and Archival
- Customizable Reporting
- Numerous Easy-to-Read Dashboards
- Multi-Tenant by Design
- Integrations for API, Syslog and Other Log Sources
- Inventory and Security Assessments
- Scalable 'Deploy Anywhere' Model
- Role-based Access Control
- Log Storage and Archival
- Customizable Reporting
- Numerous Easy-to-Read Dashboards
- Multi-Tenant by Design
- Integrations for API, Syslog and Other Log Sources
- Inventory and Security Assessments
- Scalable 'Deploy Anywhere' Model
Fully Ready for MSP’s
The platform is fully ready for MSP’s and MSSP’s, providing automated deployment, robust multi-tenancy features, and SOC dashboards with aggregated data from all your tenants.
Fully Ready for MSP’s
The platform is fully ready for MSP’s and MSSP’s, providing automated deployment, robust multi-tenancy features, and SOC dashboards with aggregated data from all your tenants.
Easy to Deploy
- No minimum commitment to start - pay as you go
- Flexible hosting options
- Automated deployment
- An extensive library of ready-to-go cloud and syslog integrations
- Integration with your RMM and service desk
- No minimum commitment to start - pay as you go
- Flexible hosting options
- Automated deployment
- An extensive library of ready-to-go cloud and syslog integrations
- Integration with your RMM and service desk
Cover All Your Technology
- Visibility across your network, cloud and endpoints
- Multi-tenant by design
- Integrated with your EDR
- Search and report across all of your tenants
- Evidence-based security with deep visibility, deception and NDR
- Visibility across your network, cloud and endpoints
- Multi-tenant by design
- Integrated with your EDR
- Search and report across all of your tenants
- Evidence-based security with deep visibility, deception and NDR
24x7 Security Operations
- Build your own SOC or use our 24x7 team
- Malware analysis and DFIR
- SOC automation and SecOps AI
- Cyber experts for advanced incident response and hunting
- Customizable reporting and dashboards
- Build your own SOC or use our 24x7 team
- Malware analysis and DFIR
- SOC automation and SecOps AI
- Cyber experts for advanced incident response and hunting
- Customizable reporting and dashboards
Easy to Deploy
- No minimum commitment to start - pay as you go
- Flexible hosting options
- Automated deployment
- An extensive library of ready-to-go cloud and syslog integrations
- Integration with your RMM and service desk
- No minimum commitment to start - pay as you go
- Flexible hosting options
- Automated deployment
- An extensive library of ready-to-go cloud and syslog integrations
- Integration with your RMM and service desk
Cover All Your Technology
- Visibility across your network, cloud and endpoints
- Multi-tenant by design
- Integrated with your EDR
- Search and report across all of your tenants
- Evidence-based security with deep visibility, deception and NDR
- Visibility across your network, cloud and endpoints
- Multi-tenant by design
- Integrated with your EDR
- Search and report across all of your tenants
- Evidence-based security with deep visibility, deception and NDR
24x7 Security Operations
- Build your own SOC or use our 24x7 team
- Malware analysis and DFIR
- SOC automation and SecOps AI
- Cyber experts for advanced incident response and hunting
- Customizable reporting and dashboards
- Build your own SOC or use our 24x7 team
- Malware analysis and DFIR
- SOC automation and SecOps AI
- Cyber experts for advanced incident response and hunting
- Customizable reporting and dashboards
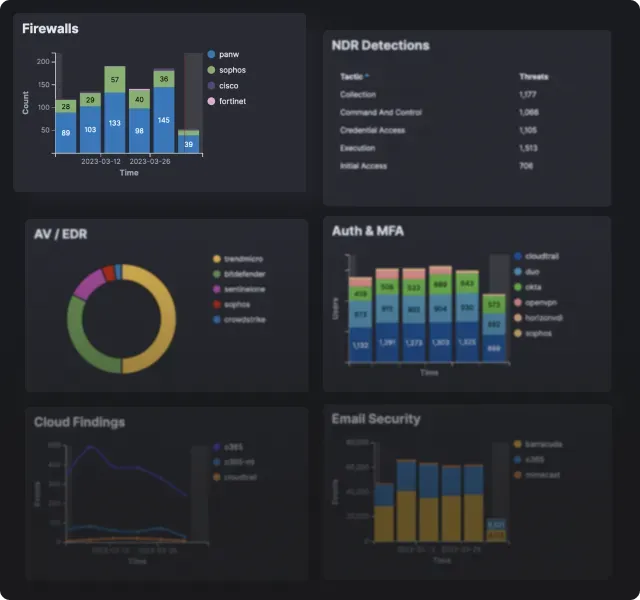
Powerful Analyst Toolset
Use a complete SecOps toolset as part of your next-generation SIEM, empowering your analysts with deep visibility and evidence-based investigations.
Powerful Analyst Toolset
Use a complete SecOps toolset as part of your next-generation SIEM, empowering your analysts with deep visibility and evidence-based investigations.
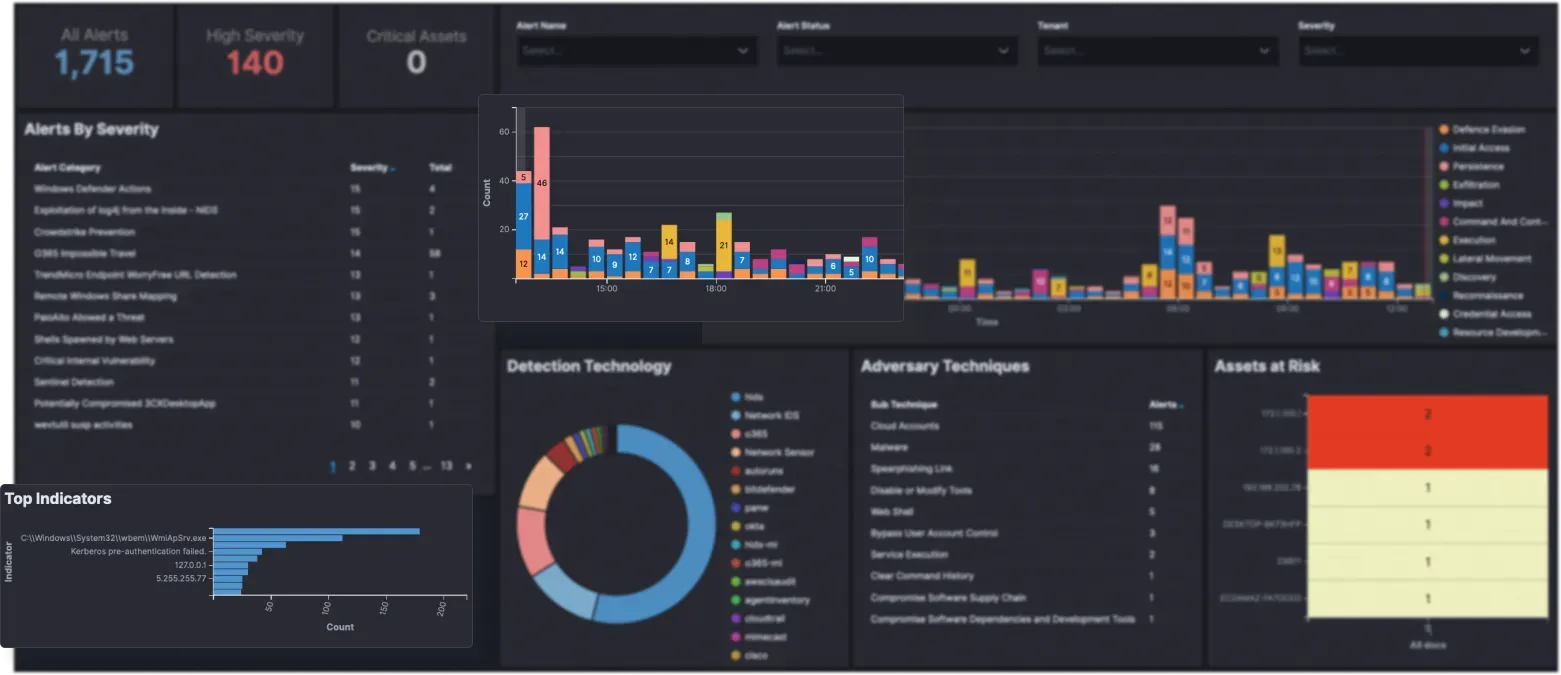
Powerful Analyst Toolset
Use a complete SecOps toolset as part of your next-generation SIEM, empowering your analysts with deep visibility and evidence-based investigations.
Powerful Analyst Toolset
Use a complete SecOps toolset as part of your next-generation SIEM, empowering your analysts with deep visibility and evidence-based investigations.

Flexible Customer Reports
Compliment your SIEM with risk-driven reporting and security posture management. The portal provides real-time reports on detected threats, security incidents, security controls efficiency and compliance metrics.
Flexible Customer Reports
Compliment your SIEM with risk-driven reporting and security posture management. The portal provides real-time reports on detected threats, security incidents, security controls efficiency and compliance metrics.
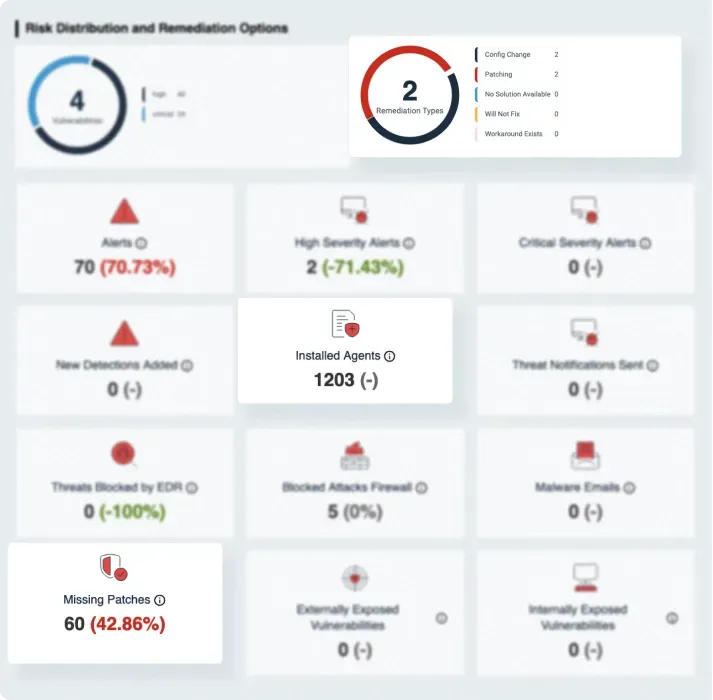
Flexible Customer Reports
Compliment your SIEM with risk-driven reporting and security posture management. The portal provides real-time reports on detected threats, security incidents, security controls efficiency and compliance metrics.
Flexible Customer Reports
Compliment your SIEM with risk-driven reporting and security posture management. The portal provides real-time reports on detected threats, security incidents, security controls efficiency and compliance metrics.

Deploy Our Platform in Minutes
Our platform can be activated in minutes, immediately producing detections and insights, and providing you unprecedented visibility across your entire environment.
Deploy Our Platform in Minutes
Our platform can be activated in minutes, immediately producing detections and insights, and providing you unprecedented visibility across your entire environment.
- Automated deployment options
- White-labelled Customer Portal and Analyst Console
- A lightweight agent deploys in seconds without any impact on user productivity
- Easy installation, management, and support, 100% cloud-based platform
- Multi-tenant environment, search and report across all of your tenants
- Integrated threat intel, dark web monitoring, vulnerability management and many other features
- Automated deployment options
- White-labelled Customer Portal and Analyst Console
- A lightweight agent deploys in seconds without any impact on user productivity
- Easy installation, management, and support, 100% cloud-based platform
- Multi-tenant environment, search and report across all of your tenants
- Integrated threat intel, dark web monitoring, vulnerability management and many other features
Gain Deep Visibility
Gain Deep Visibility
Security Operations
- Alerts and Events grouped by MITRE ATT&CK
- Work from Home statistics
- Inventory (all onboarded systems and log sources)
- Emerging threats and global threat activity
- User activity report
- Vulnerability management
- Network activity report
- Dark Web leaks
- Exposures and vulnerabilities
- Machine Learning findings
- Compliance controls and events
- Attack Surface Management
- Essential Eight controls and events
- A single pane of glass for all tools
- Alerts and Events grouped by MITRE ATT&CK
- Work from Home statistics
- Inventory (all onboarded systems and log sources)
- Emerging threats and global threat activity
- User activity report
- Vulnerability management
- Network activity report
- Dark Web leaks
- Exposures and vulnerabilities
- Machine Learning findings
- Compliance controls and events
- Attack Surface Management
- Essential Eight controls and events
- A single pane of glass for all tools
Corporate endpoints
- Endpoint security events
- Command line executions
- MITRE ATT&CK events
- Missing security patches
- CIS security controls
- Active Directory events
- File Downloads
- Installed software
- Registry and System file changes
- Process list
- Endpoint security events
- Command line executions
- MITRE ATT&CK events
- Missing security patches
- CIS security controls
- Active Directory events
- File Downloads
- Installed software
- Registry and System file changes
- Process list
Public Cloud
- Office365 Summary
- Microsoft Compliance Centre
- AzureAD Active Directory events
- User activity (O365)
- Threat intelligence events
- Azure/AWS Cloud Inventory
- AzureAD Threat Intelligence
- Privileged user activity
- SharePoint activity
- Security configuration benchmarks
- OneDrive activity
- Misconfigurations and exposures
- Exchange Online activity
- Publicly exposed systems
- Office365 Summary
- Microsoft Compliance Centre
- AzureAD Active Directory events
- User activity (O365)
- Threat intelligence events
- Azure/AWS Cloud Inventory
- AzureAD Threat Intelligence
- Privileged user activity
- SharePoint activity
- Security configuration benchmarks
- OneDrive activity
- Misconfigurations and exposures
- Exchange Online activity
- Publicly exposed systems
Network
- Network threats and intrusions
- SMB Events
- Network traffic flows
- Notable traffic flows
- Threat intelligence events
- Network tunnels
- DNS Events
- User behaviour
- DHCP Events
- Remote access
- Network threats and intrusions
- SMB Events
- Network traffic flows
- Notable traffic flows
- Threat intelligence events
- Network tunnels
- DNS Events
- User behaviour
- DHCP Events
- Remote access



