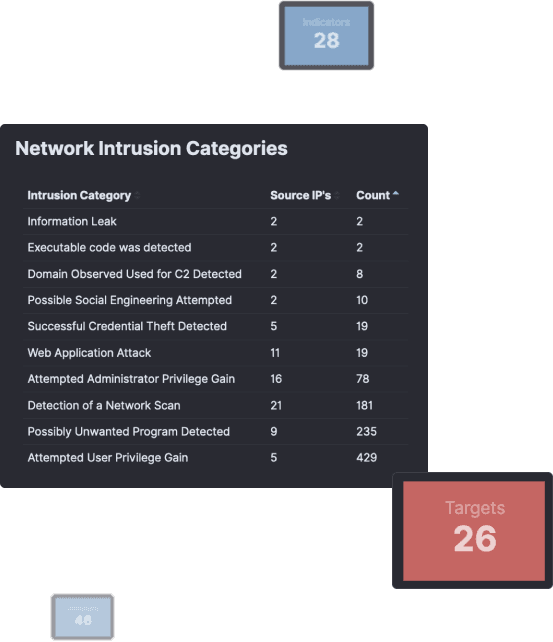
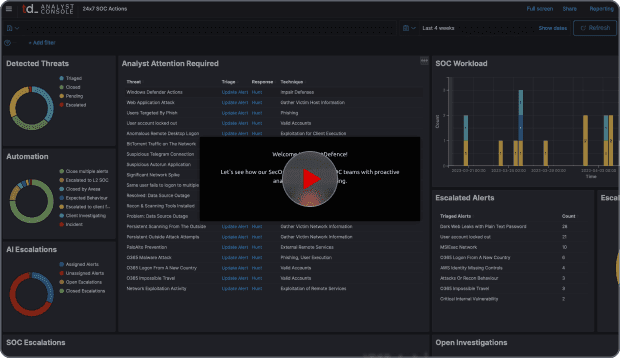
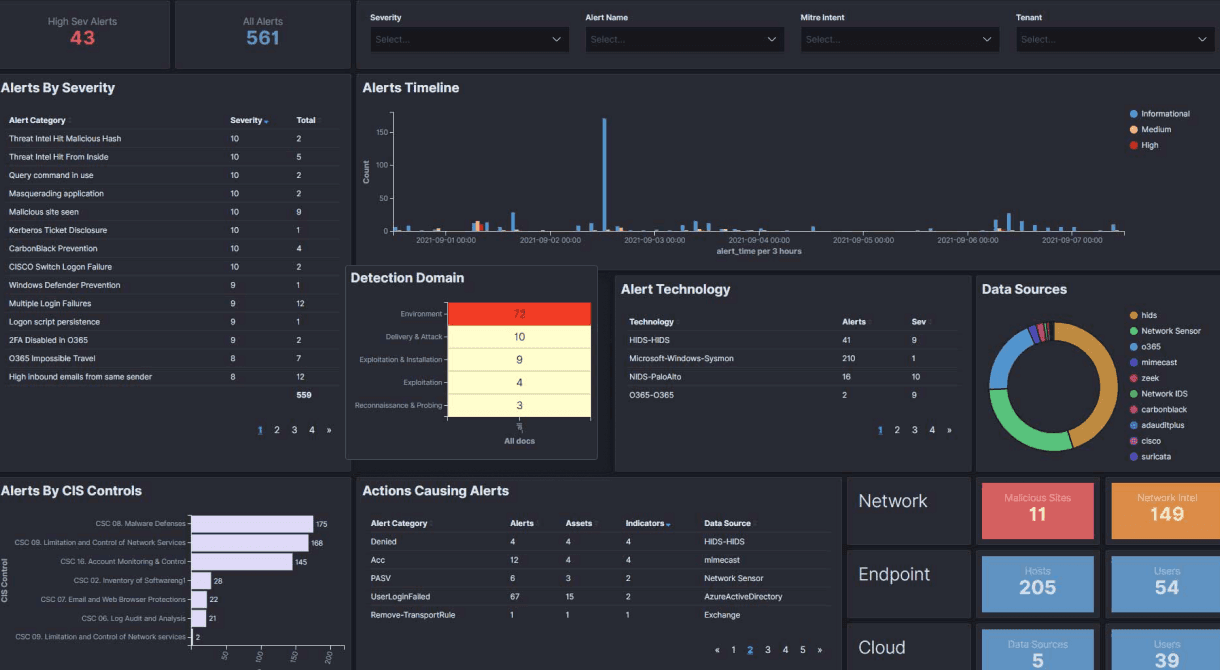
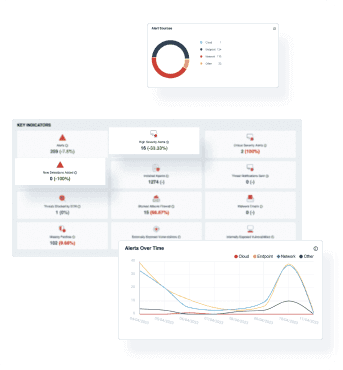
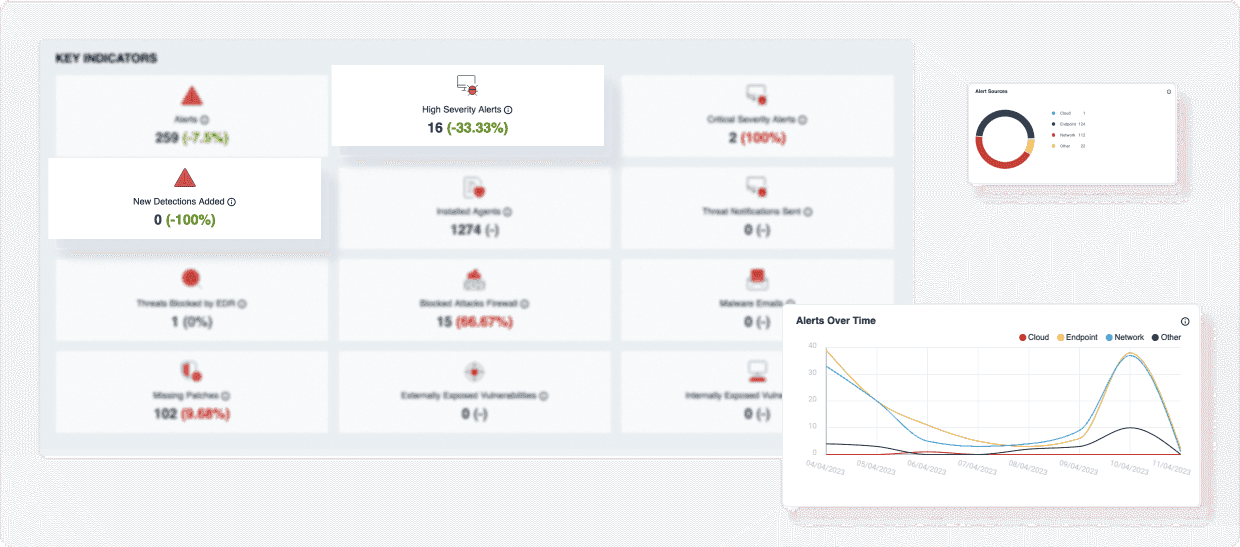
Businesses are constantly being targeted by hackers these days. The problem is, most SMB’s do not have sufficient resources to implement and operate a full-on, enterprise-grade Security Operations capability.
Most of MSP-focused ‘managed SOC’ solutions on the market are designed as a wholesale solutions - while some of them might be easy to deploy, they only only include a fraction of technologies of capabilities required for an enterprise-grade Security Operations, and usually you feel like you need to give up something and compromise on visibility that you can achieve.
Furthermore, usually MSP’s are usually expected to take the service as it is - it rarely can be customised to what your customers really need.
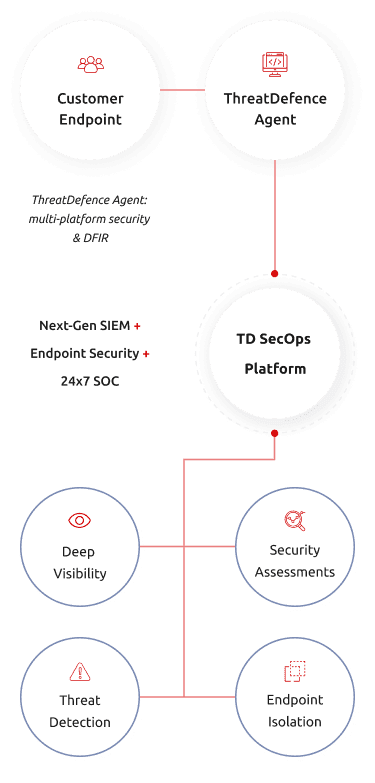
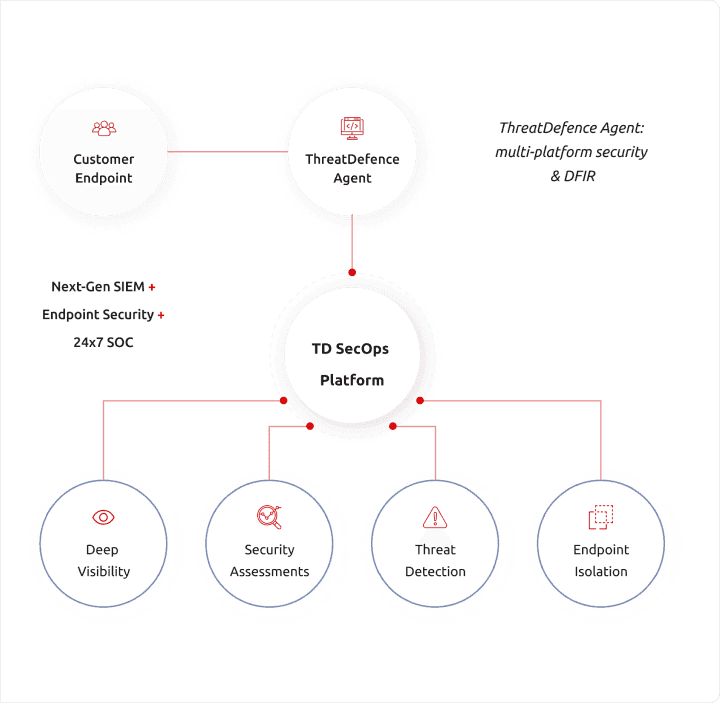
ThreatDefence is the only solution that provides end-to-end Security Operations platform
Scale Your Cyber Security Capability
We have everything ready to go for you – people, process, technology, as well as sales and marketing collateral and MSSP service packages to deliver to your customers. Our cyber security experts will work with your team to launch your cyber security program and get you started. We do not require any minimum commitment from you and we are ready to onboard your customers immediately.
Our technology is 100% cloud-based and can be deployed to your customers’ environments right now, providing full coverage across endpoint, network, syslog, cloud and other log sources.
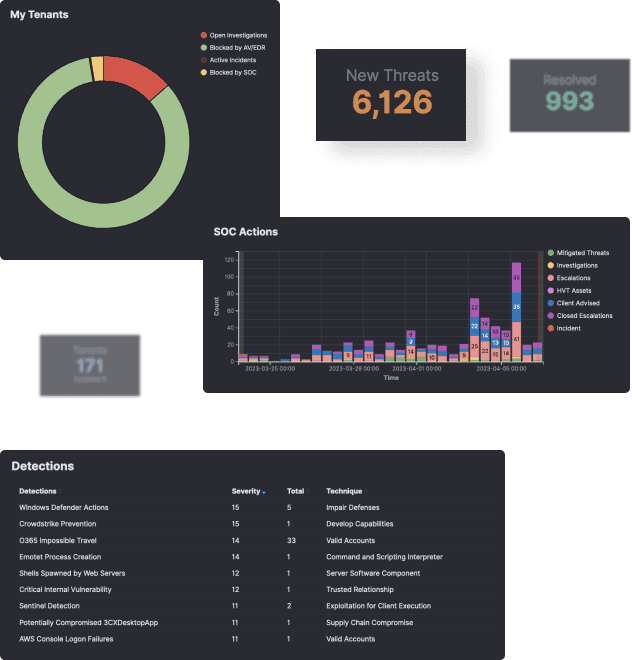
True Multi-Tenancy
You can manage hundreds of tenants within our platform, leveraging all platform features in a true multi-tenancy mode.
You can quickly search and run investigations across hundreds of organizations at once, providing your team with insights across your entire customer base and dramatically reducing your MTTD and MTTR.
24x7 SOC - We Become Part Of Your Team
Our SOC-as-a-Service provides MSPs with scalable options to grow your cyber security business. We offer multiple options on how you can get started. You can completely outsource your service to us, or use us as the last line of your response capability and get your team to handle initial alerts and customer requests.
Continuous Monitoring
We monitor security events and detect threats in real-time, 24 hours a day. Our system processes your data non-stop and provide correlations and detections in real-time.Security Geeks
We hire cybersecurity experts who love technology and seamlessly integrate with your team to keep you secure.Threat Intelligence
We understand cyber security and prioritize real-world detection scenarios over simple alerts and thresholds.
WorkingTogether
You will have direct access to our threat hunters, incident responders and platform engineers who will help to get your requests resolved in real-time.
When it comes to incident response, we work with your technical team to contain cyber threats as soon as possible. We will work together to prioritize quick threat containment and root cause identification. As the breach is contained, we will collect evidence, determine instances of data exfiltration, conduct forensic analysis and prepare a detailed post-incident review.

How it works
Our platform is 100% cloud-based and is available to be used immediately by you and your customers. It only takes a few simple steps to start using our solutions:
Our Partners About Us

Roman ShragaCTO, Klik Solutions

Principal ConsultantLeading Australian MSP

Jacob ThankachenCEO, CybrHawk
Value Proposition For Your Customers
Unfortunately, many businesses lack visibility into their network activity, leaving them unable to confidently detect cyber threats or fully understand the extent of the damage in the event of a compromise.
If your customer's organization were to experience a breach tomorrow, do you have a plan in place? Security Incident Response is a costly endeavor that can take weeks of security experts' time at premium rates, consuming a significant amount of your business's resources and making recovery efforts extremely time-consuming.
The cost of being protected is not high - With our SOC as a Service you can provide your customers with:
- Ongoing security monitoring of systems and networks, detecting any malicious activity.
- Dark Web monitoring, providing proactive notifications if user accounts are compromised.
- Continuous forensic recording of security events, allowing quick investigations and breach containment.
- 24x7 Security Operations Centre, providing incident response and guidance during a data breach.
White Labeled Reporting
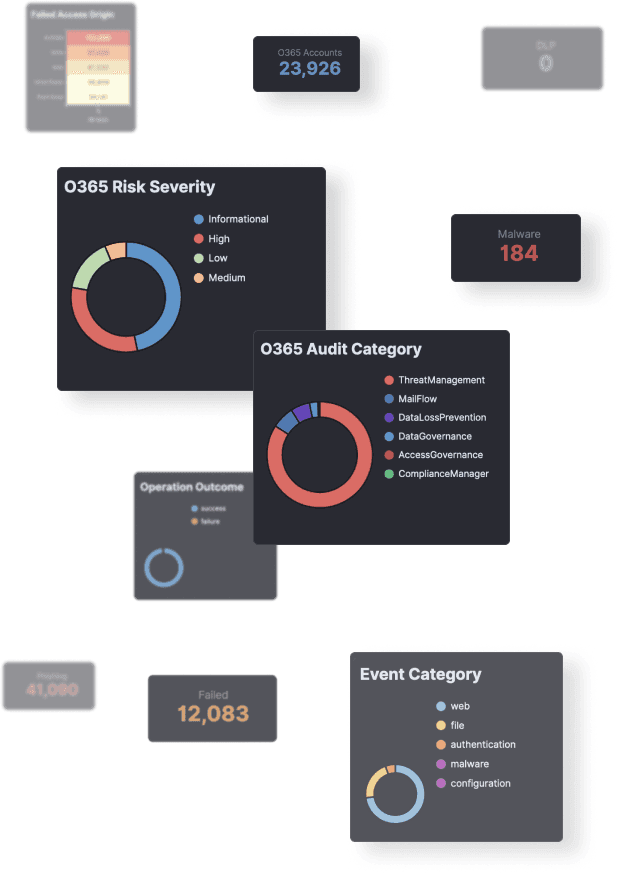
We provide automated weekly and monthly reporting to your customers based on their operational and compliance needs.
Our reporting covers security posture overview, ongoing operational issues, security trends over time, and various compliance frameworks such as IS027001, PCI DSS, Essential Eight and others.
All reports can be white labelled - just send us your logo, and we will do the rest.
Start Today For Free
At ThreatDefence, we know that seeing is believing. Many products claim to do wonderful things but disappoint when the rubber hits the road. For us, the opposite is true. When MSP’s see ThreatDefence live on their security data, the potential suddenly comes alive and the value appears.
We can run a Proof of Value for your own infrastructure, as well as for 1-2 of your customers. We will create a multi-tenant instance for you and will onboard your data. You will get immediate access to all dashboards, alerts and reports, as well as to our 24×7 SOC team. If you like what you see, you can continue using the service every month – and your first month will be free!