Transform Noise Into Evidence
Managed Network Detection and Response for your datacenter, virtual, WAN, and branch networks.
Transform Noise Into Evidence
Managed Network Detection and Response for your datacenter, virtual, WAN, and branch networks.

Transform Noise Into Evidence
Managed Network Detection and Response for your datacenter, virtual, WAN, and branch networks.
Transform Noise Into Evidence
Managed Network Detection and Response for your datacenter, virtual, WAN, and branch networks.

Empower Your SecOps with Open NDR Platform
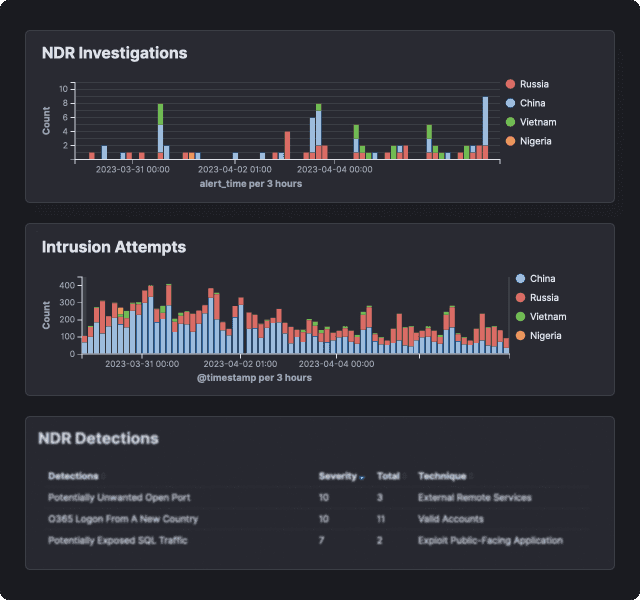
Record Data as Evidence
Eliminate noise and record months of evidence, leaving nothing to the unknown.Detect Most Elusive Threats
Advanced detection capabilities and rich threat intelligence leave attackers with no chance.Threat Hunt Like a Pro
Get data from all sources in a single view, and follow attackers as they move laterally, visualising the entire extent of the attack.Respond With Confidence
Assess the full extent of the attack, view the complete actions of the attacker and respond within seconds.
Record Data as Evidence
Eliminate noise and record months of evidence, leaving nothing to the unknown.Detect Most Elusive Threats
Advanced detection capabilities and rich threat intelligence leave attackers with no chance.Threat Hunt Like a Pro
Get data from all sources in a single view, and follow attackers as they move laterally, visualising the entire extent of the attack.Respond With Confidence
Assess the full extent of the attack, view the complete actions of the attacker and respond within seconds.
Deep Network Visibility
ThreatDefence network sensor is a real-time Network Detection and Response(NDR) solution which can be deployed to monitor inline network traffic on-premises or in-cloud, inspecting both horizontal and vertical traffic flows.
The NDR detects even the most concealed activities and utilises our machine learning technology to identify unknown threats, lateral movement and malicious insider behaviour.
Deep Network Visibility
ThreatDefence network sensor is a real-time Network Detection and Response(NDR) solution which can be deployed to monitor inline network traffic on-premises or in-cloud, inspecting both horizontal and vertical traffic flows.
The NDR detects even the most concealed activities and utilises our machine learning technology to identify unknown threats, lateral movement and malicious insider behaviour.
Deep Network Visibility
ThreatDefence network sensor is a real-time Network Detection and Response(NDR) solution which can be deployed to monitor inline network traffic on-premises or in-cloud, inspecting both horizontal and vertical traffic flows.
The NDR detects even the most concealed activities and utilises our machine learning technology to identify unknown threats, lateral movement and malicious insider behaviour.
Deep Network Visibility
ThreatDefence network sensor is a real-time Network Detection and Response(NDR) solution which can be deployed to monitor inline network traffic on-premises or in-cloud, inspecting both horizontal and vertical traffic flows.
The NDR detects even the most concealed activities and utilises our machine learning technology to identify unknown threats, lateral movement and malicious insider behaviour.

Forensic Captures
Detailed recording of network metadata and full packet-level communications for investigations and forensic evidence gatheringUser Behavior
_NETWORK analyses user and machine behavior that provides insights based on detected deviations and anomaliesNetwork Baseline
Get full visibility into your network and see who is talking to what you cto crated a complete baseline for all internal and external connections
See Everything - SMB, DNS, SCADA and More
Gain complete visibility into all enterprise services with protocol-level awareness - see traffic from databases, remote services, Active Directory, industrial equipment and IoT.
See Everything - SMB, DNS, SCADA and More
Gain complete visibility into all enterprise services with protocol-level awareness - see traffic from databases, remote services, Active Directory, industrial equipment and IoT.
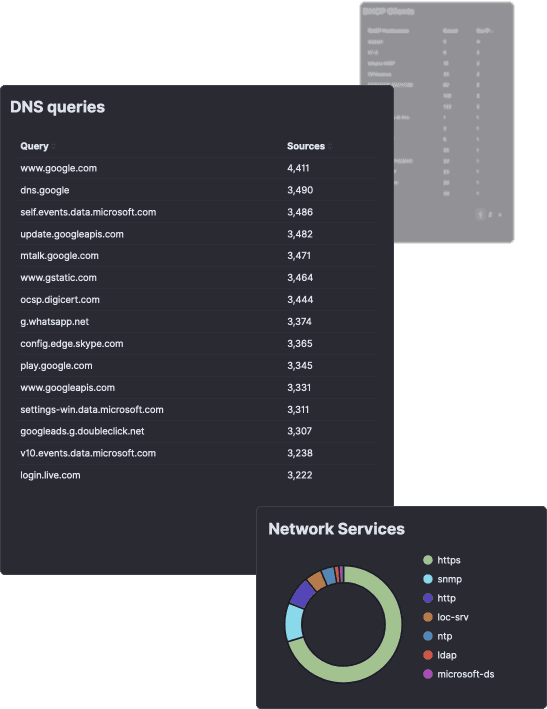
See Everything - SMB, DNS, SCADA and More
Gain complete visibility into all enterprise services with protocol-level awareness - see traffic from databases, remote services, Active Directory, industrial equipment and IoT.
See Everything - SMB, DNS, SCADA and More
Gain complete visibility into all enterprise services with protocol-level awareness - see traffic from databases, remote services, Active Directory, industrial equipment and IoT.

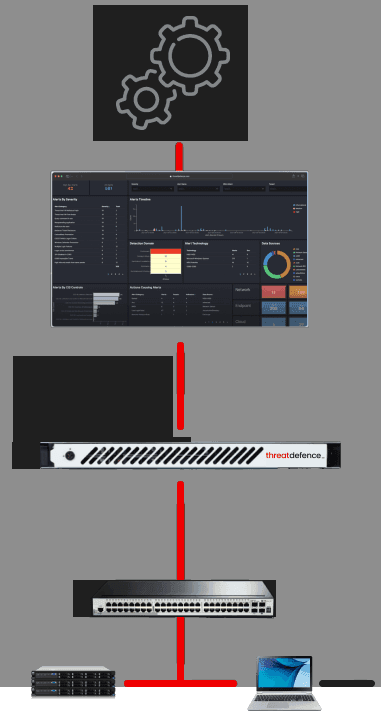
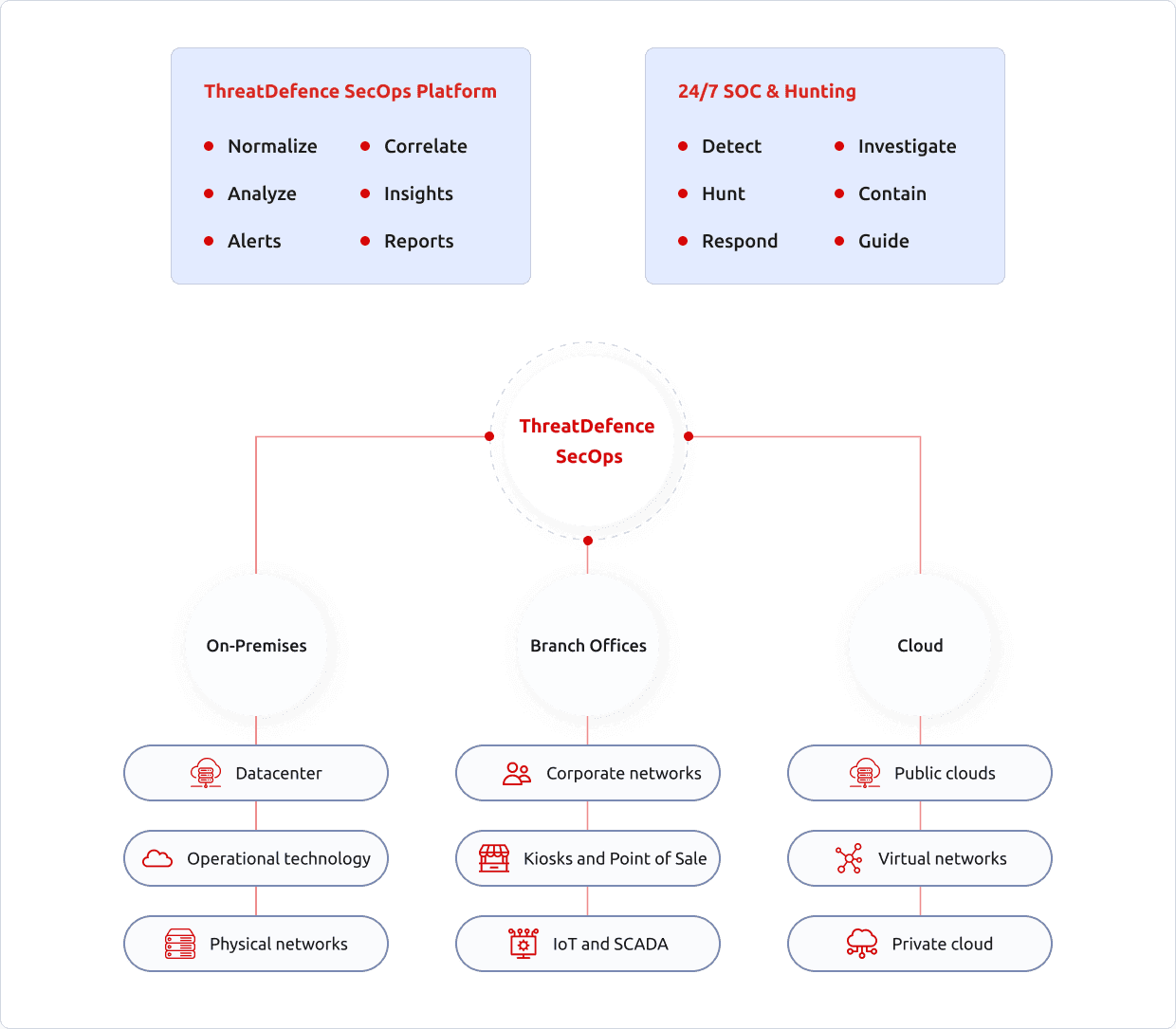
HOW IT WORKS
ThreatDefence NDR integrates out-of-band into your network segments and inspects both inbound and outbound traffic in your environment in real time. The sensor appliances can tap into your branch offices, WAN segments and cloud networks.
All data is integrated into our SecOps platform where threats are detected, and the blocked on the network perimeter and within the network in real time.
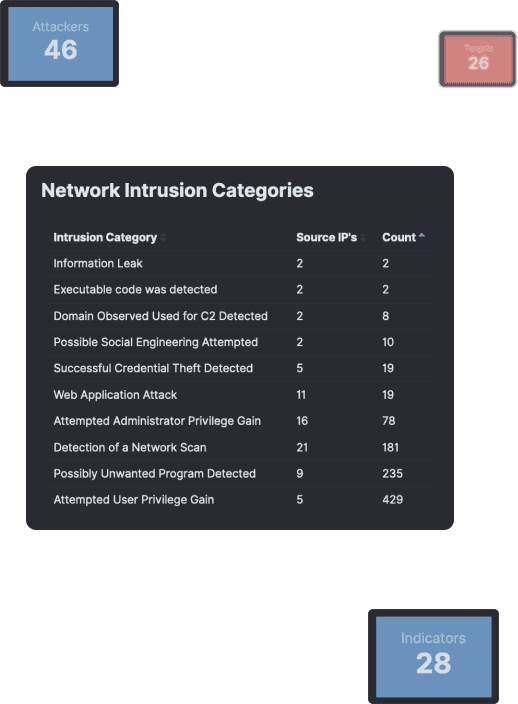
Continuous Evidence
NDR brings full forensic investigation capability into your environment for advanced investigations and evidence collection.
Retain as much data as you need to provide complete assurance to your business.
Continuous Evidence
NDR brings full forensic investigation capability into your environment for advanced investigations and evidence collection.
Retain as much data as you need to provide complete assurance to your business.
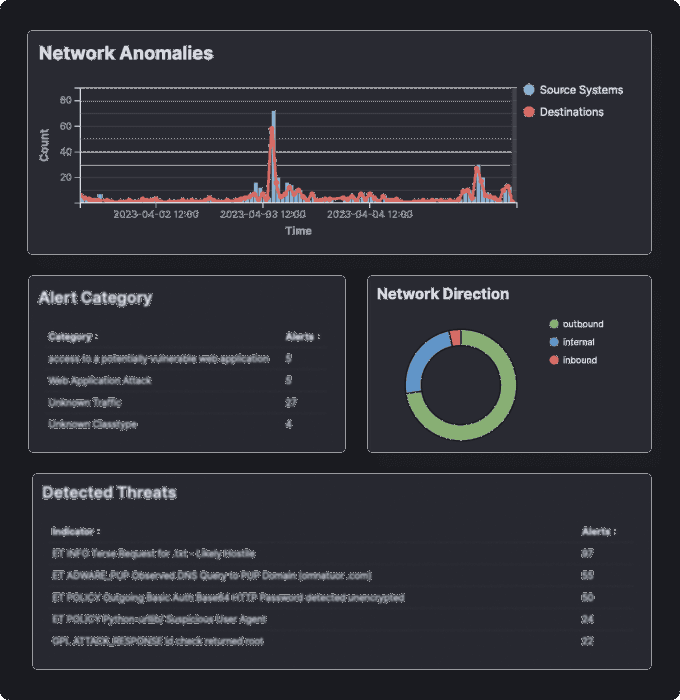
Continuous Evidence
NDR brings full forensic investigation capability into your environment for advanced investigations and evidence collection.
Retain as much data as you need to provide complete assurance to your business.
Continuous Evidence
NDR brings full forensic investigation capability into your environment for advanced investigations and evidence collection.
Retain as much data as you need to provide complete assurance to your business.

In Depth Detections and Analytics
Detect advanced adversary tactics and techniques, including:
In Depth Detections and Analytics
Detect advanced adversary tactics and techniques, including:
- Lateral movement
- Command & Control traffic
- Backdoors and tunnels
- Malware and botnet connections
- Internal port scanning and reconnaissance
- Password brute forcing
- Unauthorised remote access tools
- Rogue devices
- Lateral movement
- Command & Control traffic
- Backdoors and tunnels
- Malware and botnet connections
- Internal port scanning and reconnaissance
- Password brute forcing
- Unauthorised remote access tools
- Rogue devices
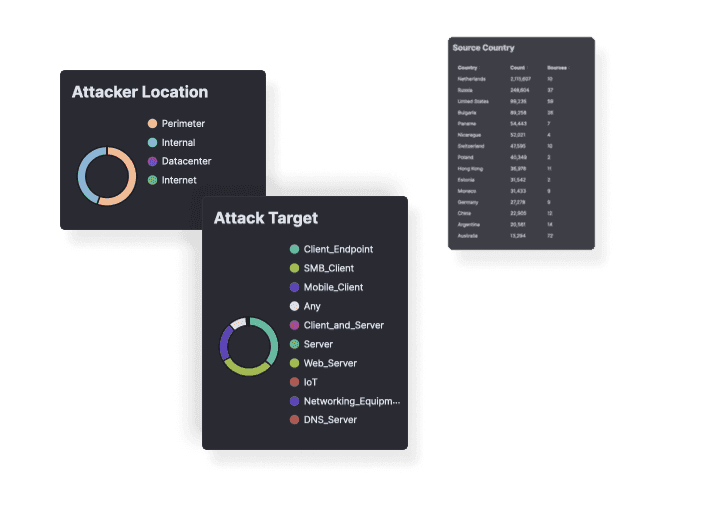
In Depth Detections and Analytics
Detect advanced adversary tactics and techniques, including:
In Depth Detections and Analytics
Detect advanced adversary tactics and techniques, including:
- Lateral movement
- Command & Control traffic
- Backdoors and tunnels
- Malware and botnet connections
- Internal port scanning and reconnaissance
- Password brute forcing
- Unauthorised remote access tools
- Rogue devices
- Lateral movement
- Command & Control traffic
- Backdoors and tunnels
- Malware and botnet connections
- Internal port scanning and reconnaissance
- Password brute forcing
- Unauthorised remote access tools
- Rogue devices

Threat Hunting
Use network evidence to detect hidden and unknown hacker activity, including zero-day attacks, lateral movement, insider threats, and impersonation attacks.
Threat Hunting
Use network evidence to detect hidden and unknown hacker activity, including zero-day attacks, lateral movement, insider threats, and impersonation attacks.

Threat Hunting
Use network evidence to detect hidden and unknown hacker activity, including zero-day attacks, lateral movement, insider threats, and impersonation attacks.
Threat Hunting
Use network evidence to detect hidden and unknown hacker activity, including zero-day attacks, lateral movement, insider threats, and impersonation attacks.








