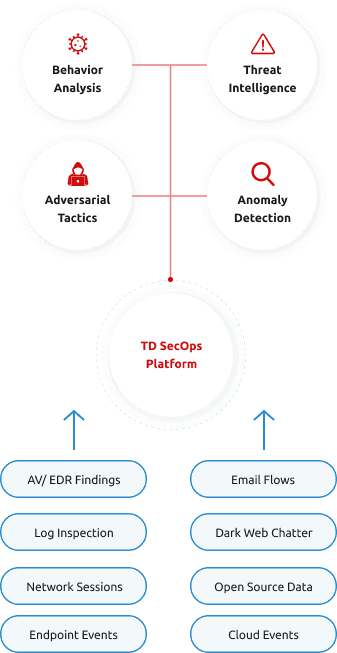
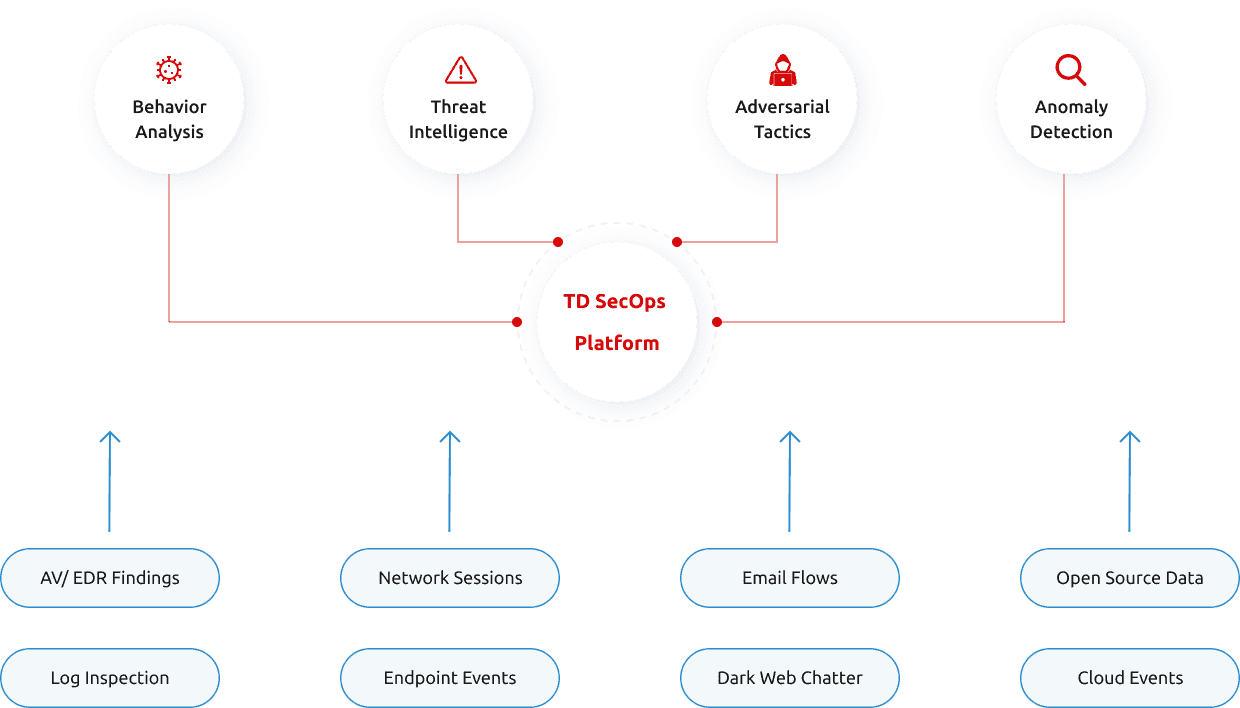
Our endpoint analysis employs endpoint agents to monitor and detect potential attacker activity, such as malware usage and other malicious techniques. We cover a broad range of operating systems, including Windows, macOS, and Linux, supporting both on-premises and cloud-based deployment options.
What You Get:
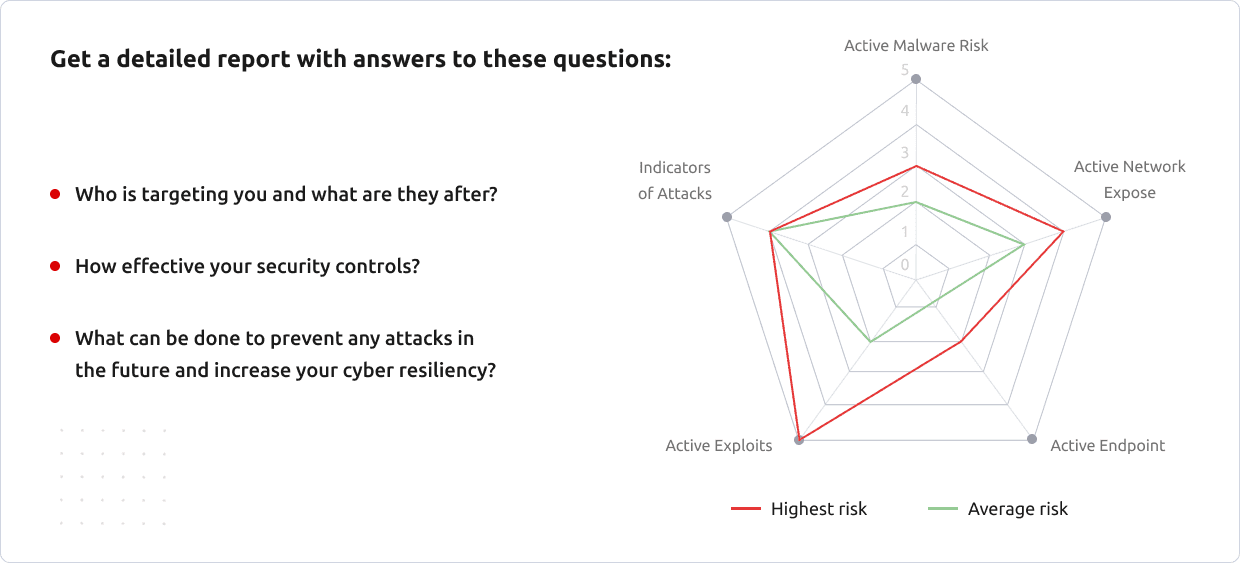
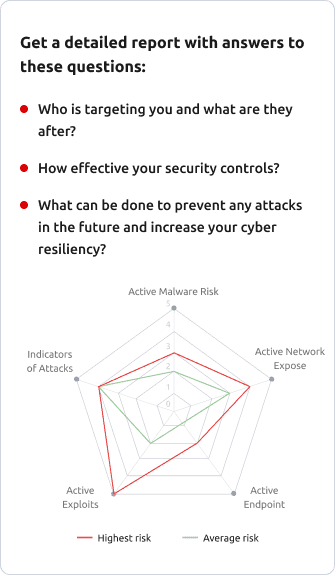
You will get a comprehensive review of your environment empowered by our real-time security analytics. We review your infrastructure, systems, networks, applications and cloud system to quickly determine the presence of current or past attacks.
During the assessment, we integrate all your security data that we can possibly reach into, including data that directly resides within your network and on your endpoints, as well as external data such as cloud workloads, SaaS applications, Dark Web breaches, compromised credentials, external vulnerabilities, as well as weaknesses and exposures related to third-party organisations in your supply chain.
Why ThreatDefence for Compromise Assessment
Our Compromise Assessment combines our deep visibility technology with our extensive experience of responding to sophisticated breaches and investigating security incidents. During the assessment, our focus is on a deep, forensic analysis that goes beyond the standard scope of common security tools.
What Our Customers Say

Ramesh NaiduChief Operating Officer, Vigilant Asia

Osman HafizCyber Security Consultant, Mekdam Technology
HOW IT WORKS
Areas of Concern
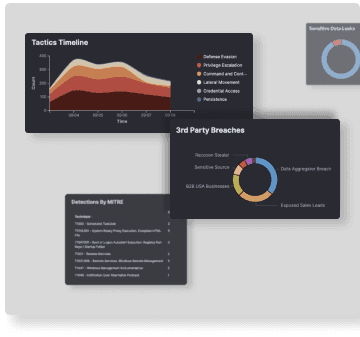
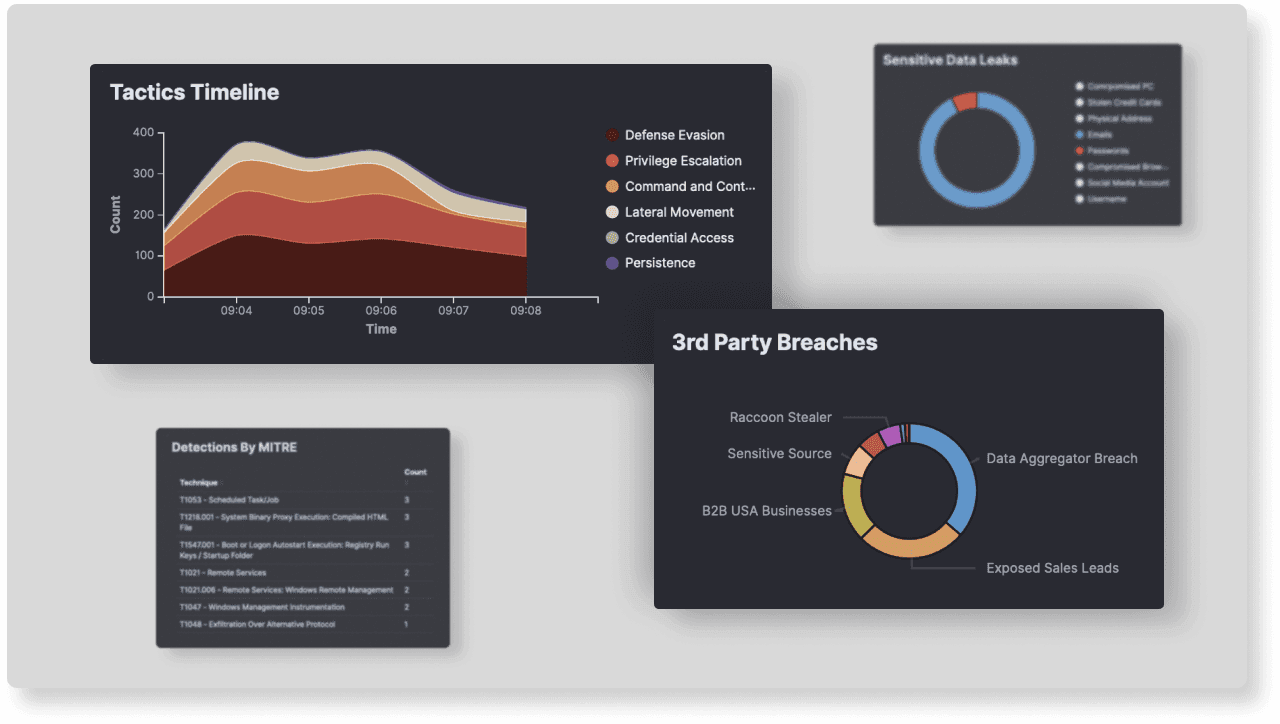
Although many organizations still prioritize their protection techniques to detect threats based on a 'point in time' analysis of malicious behavior, intruders rarely execute their entire mission in a few minutes or hours. In fact, the most sophisticated intruders often persist for months or years at a time.
Time series analysis is the key factor in detecting compromises, as many persistent threat actors adopted great operational security techniques. Targeting an extended window of time to expose numerous attacker actions, from initial unauthorized access to ultimate mission accomplishment, allows us to detect and contain most sophisticated adversaries.