Endpoint Visibility and DFIR at Scale
Hunt the most elusive cyber threats regardless where your data or users reside.
Endpoint Visibility and DFIR at Scale
Hunt the most elusive cyber threats regardless where your data or users reside.

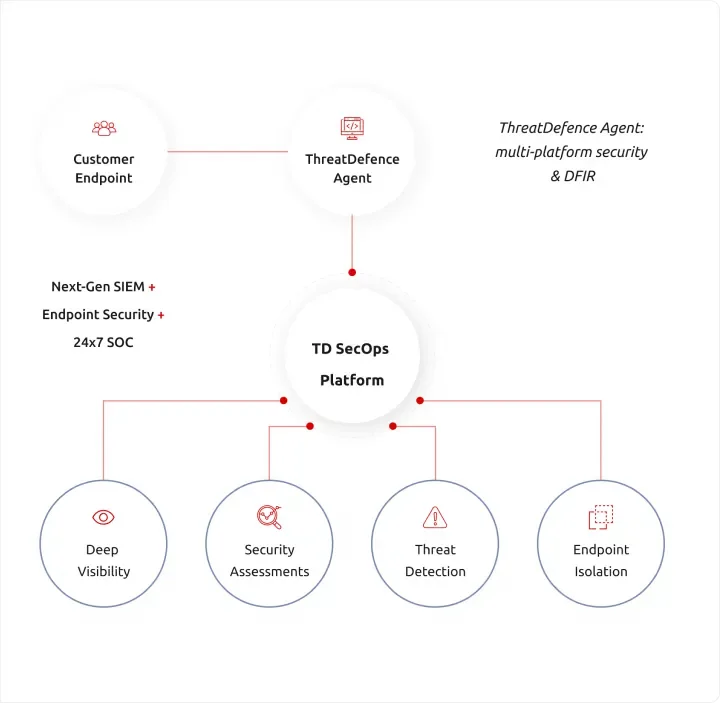
Gain Deep Endpoint Visibility
ThreatDefence Agent enables you to quickly and easily get visibility across your endpoints. The agent can be deployed in few clicks, and will immediately start sending endpoint logs from your clients' devices to our cloud platform for advanced threat detection and response.
Gain Deep Endpoint Visibility
ThreatDefence Agent enables you to quickly and easily get visibility across your endpoints. The agent can be deployed in few clicks, and will immediately start sending endpoint logs from your clients' devices to our cloud platform for advanced threat detection and response.

Gain Deep Endpoint Visibility
ThreatDefence Agent enables you to quickly and easily get visibility across your endpoints. The agent can be deployed in few clicks, and will immediately start sending endpoint logs from your clients' devices to our cloud platform for advanced threat detection and response.
Gain Deep Endpoint Visibility
ThreatDefence Agent enables you to quickly and easily get visibility across your endpoints. The agent can be deployed in few clicks, and will immediately start sending endpoint logs from your clients' devices to our cloud platform for advanced threat detection and response.

Gain Deep Endpoint Visibility
ThreatDefence Agent enables you to quickly and easily get visibility across your endpoints. The agent can be deployed in few clicks, and will immediately start sending endpoint logs from your clients' devices to our cloud platform for advanced threat detection and response.
Gain Deep Endpoint Visibility
ThreatDefence Agent enables you to quickly and easily get visibility across your endpoints. The agent can be deployed in few clicks, and will immediately start sending endpoint logs from your clients' devices to our cloud platform for advanced threat detection and response.

Gain Deep Endpoint Visibility
ThreatDefence Agent enables you to quickly and easily get visibility across your endpoints. The agent can be deployed in few clicks, and will immediately start sending endpoint logs from your clients' devices to our cloud platform for advanced threat detection and response.
Gain Deep Endpoint Visibility
ThreatDefence Agent enables you to quickly and easily get visibility across your endpoints. The agent can be deployed in few clicks, and will immediately start sending endpoint logs from your clients' devices to our cloud platform for advanced threat detection and response.

When Prevention Fails...
Hackers are proficient in bypassing security tools. When your prevention mechanisms fail, your only defense is evidence-based visibility.
When Prevention Fails...
Hackers are proficient in bypassing security tools. When your prevention mechanisms fail, your only defense is evidence-based visibility.
| Attack type | BEST EDR PRODUCTS | Other EDR products | SIEM/SOC | Visibility + Secops |
|---|---|---|---|---|
| Common threats (malware) | 100% | 70% | 100% | 100% |
| Sophisticated breaches (well-organized hackers) | 10% | 0% | 30% | 100% |
| Zero day Attacks (Exchange ProxyShell, log4shell) | 0% | 0% | 20% | 100% |
| Accounts takeovers (cloud, endpoint, network) | 0% | 0% | 50% | 100% |
| Incident Response and Investigation | 10% | 0% | 30% | 100% |
| Supply Chain Attacks (Kaseya, FireEye) | 10% | 0% | 20% | 100% |
| Attack type | BEST EDR PRODUCTS | Other EDR products | SIEM/SOC | Visibility + Secops |
|---|---|---|---|---|
| Common threats (malware) | 100% | 70% | 100% | 100% |
| Sophisticated breaches (wel... | 10% | 0% | 30% | 100% |
| Zero day Attacks (Exchange ... | 0% | 0% | 20% | 100% |
| Accounts takeovers (cloud, ... | 0% | 0% | 50% | 100% |
| Incident Response and Inves... | 10% | 0% | 30% | 100% |
| Supply Chain Attacks (Kasey... | 10% | 0% | 20% | 100% |
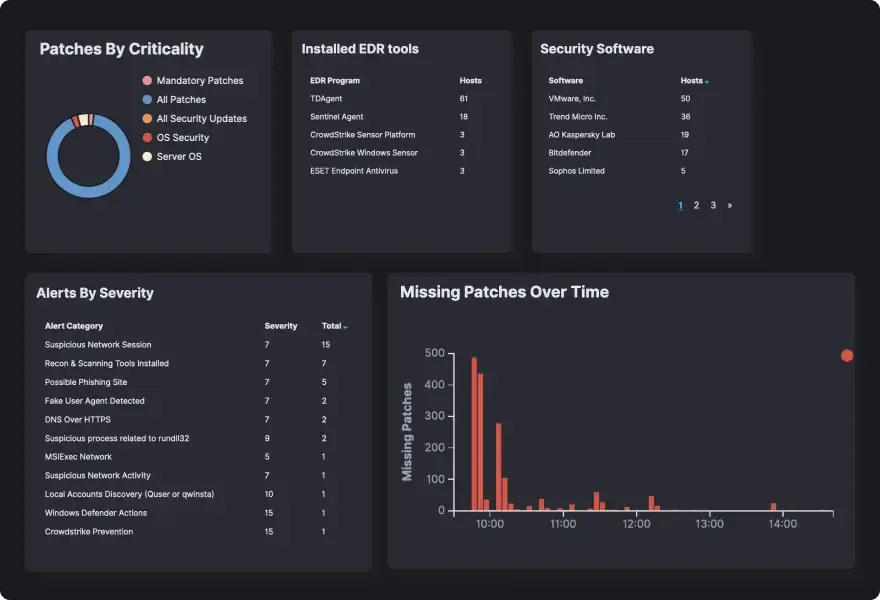
Get 100% Cyber Assurance For Endpoints
Get 100% Cyber Assurance For Endpoints
Deploy in Minutes
A variety of automated deployment options to ensure that you can cover and protect your server and user endpoints anywhere. Get Access to Your Data
See all your data and get unprecedented visibility across workstations, servers, cloud and remote endpoints. Run as a Holistic SecOps Suite
Delivered at no additional cost as part of our SecOps platform, fully integrated into your SOC processes and workflows. Manage Cyber Risk
Maintain a continuous compliance state with integrated cyber risk and security posture monitoring.
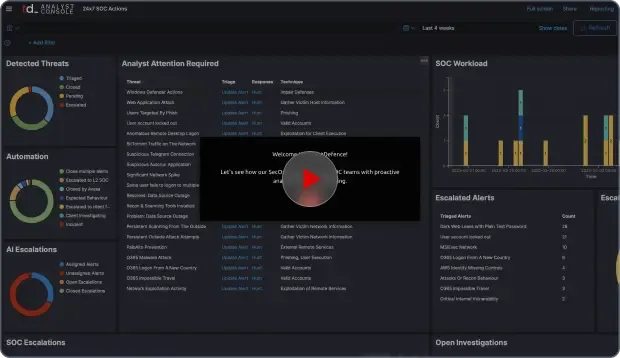
See How It Works
See how easy it is to deploy our agent and immediately start getting insights from your endpoints.
You will get visibility into active network connections, executed processes, user logons, vulnerable software and more.
See How It Works
See how easy it is to deploy our agent and immediately start getting insights from your endpoints.
You will get visibility into active network connections, executed processes, user logons, vulnerable software and more.
See How It Works
See how easy it is to deploy our agent and immediately start getting insights from your endpoints.
You will get visibility into active network connections, executed processes, user logons, vulnerable software and more.
See How It Works
See how easy it is to deploy our agent and immediately start getting insights from your endpoints.
You will get visibility into active network connections, executed processes, user logons, vulnerable software and more.
Deploy in Minutes
It only takes seconds to install a ThreatDefence agent, and it can be deployed to Windows, Linux and MacOS endpoints.
The agent is cloud-based and does not require any additional infrastructure on-premises.
Deploy in Minutes
It only takes seconds to install a ThreatDefence agent, and it can be deployed to Windows, Linux and MacOS endpoints.
The agent is cloud-based and does not require any additional infrastructure on-premises.
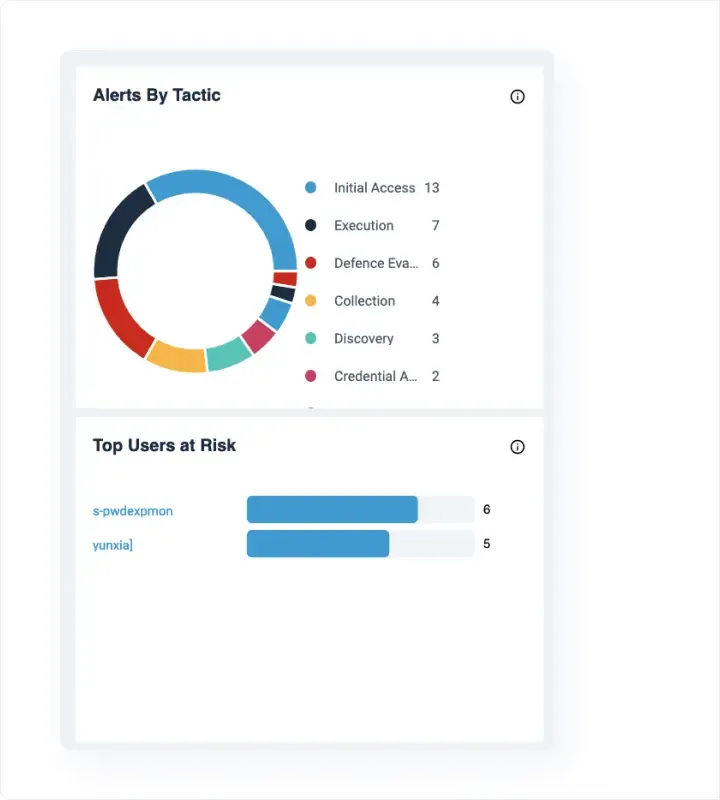

Deploy in Minutes
It only takes seconds to install a ThreatDefence agent, and it can be deployed to Windows, Linux and MacOS endpoints.
The agent is cloud-based and does not require any additional infrastructure on-premises.
Deploy in Minutes
It only takes seconds to install a ThreatDefence agent, and it can be deployed to Windows, Linux and MacOS endpoints.
The agent is cloud-based and does not require any additional infrastructure on-premises.

Augment your EDR
ThreatDefence endpoint agent derives critical insights from the endpoints in real-time, analyzing vulnerability data, system, and process usage telemetry, user behavior, and many other metrics and indicators.
The agent supports proactive detection and response capabilities, collecting critical security data from on-premises, cloud, and mobile endpoints and supplying information across the whole cyber-attack chain, from the initial reconnaissance to the malicious data exfiltration.


- Respond to threats at scale
- Live digital forensics and data acquisition
- Search across 1,000s of endpoints
- Security configuration assessments
- Put endpoints in isolation
- Evidence recording
- Respond to threats at scale
- Live digital forensics and data acquisition
- Search across 1,000s of endpoints
- Security configuration assessments
- Put endpoints in isolation
- Evidence recording
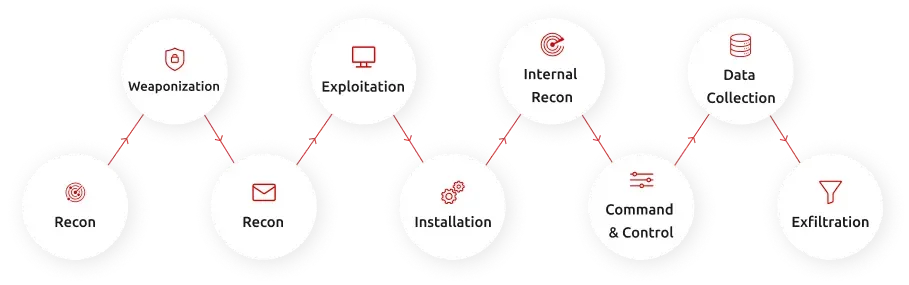

- Respond to threats at scale
- Live digital forensics and data acquisition
- Search across 1,000s of endpoints
- Security configuration assessments
- Put endpoints in isolation
- Evidence recording
- Respond to threats at scale
- Live digital forensics and data acquisition
- Search across 1,000s of endpoints
- Security configuration assessments
- Put endpoints in isolation
- Evidence recording
Threat Hunting
Our endpoint agent assists SOC teams to run searches, and investigations at a great scale.
You can get any evidence you need in seconds - watch this video and see how it works.
Threat Hunting
Our endpoint agent assists SOC teams to run searches, and investigations at a great scale.
You can get any evidence you need in seconds - watch this video and see how it works.
Threat Hunting
Our endpoint agent assists SOC teams to run searches, and investigations at a great scale.
You can get any evidence you need in seconds - watch this video and see how it works.
Threat Hunting
Our endpoint agent assists SOC teams to run searches, and investigations at a great scale.
You can get any evidence you need in seconds - watch this video and see how it works.