Cybersecurity in Healthcare: Protecting Sensitive Patient Data
Sensitive patient data is a prime target for cyber attackers. Healthcare organizations are responsible for safeguarding this information and ensuring its confidentiality, integrity, and availability. A data breach in the healthcare industry can have severe consequences, compromising not only the organization's reputation but also the health and privacy of patients.
The risks associated with the theft or exposure of sensitive patient data can be catastrophic. Patient data can include personal information, medical histories, and test results, which, if accessed by cybercriminals, can be used to commit identity theft or medical fraud. Additionally, patients may suffer from psychological and emotional distress resulting from the loss of privacy and security of their sensitive information.
Furthermore, the healthcare industry is heavily regulated, and non-compliance with data privacy laws can result in significant financial and legal consequences. Given the severity of the risks associated with sensitive patient data, healthcare organizations must take a proactive approach to cybersecurity to protect themselves and their patients.

Head of TechnologyLarge Healthcare Organization
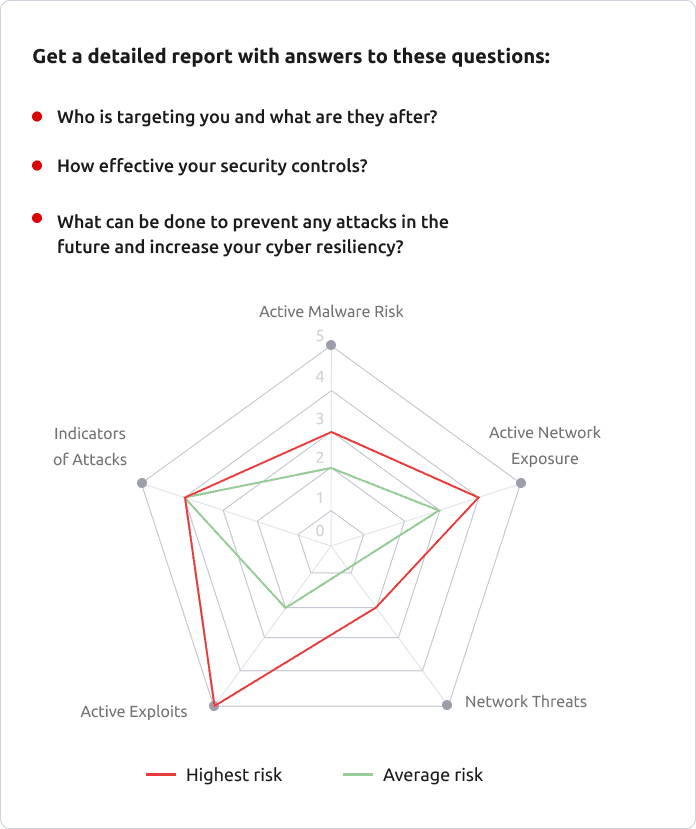
Revealing Malicious Activity
Threat actors often maintain persistent access to their victims over extended periods of time, getting business insights and stealing sensitive data. Leverage our technology as well as our experience in incident response and digital forensics to get a deep, forensic review of your organization over an extended period of time. We will analyze every endpoint, user, cloud service and network flow to discover any anomalies in your network and to ensure that your environment is not compromised.
Protecting Patients Data
We employ an evidence-based approach to security, leveraging data from across the organization to provide a holistic view of your security posture and security events. The capabilities allow security teams to quickly respond to potential threats and take action to mitigate them before they cause damage.