Integrated Attack Surface Management
Use our attack surface management solution to get a real-time view into any vulnerabilities, weaknesses, exposures, disclosures, insecure third parties and other anomalies in your Internet-facing services.
Integrated Attack Surface Management
Use our attack surface management solution to get a real-time view into any vulnerabilities, weaknesses, exposures, disclosures, insecure third parties and other anomalies in your Internet-facing services.
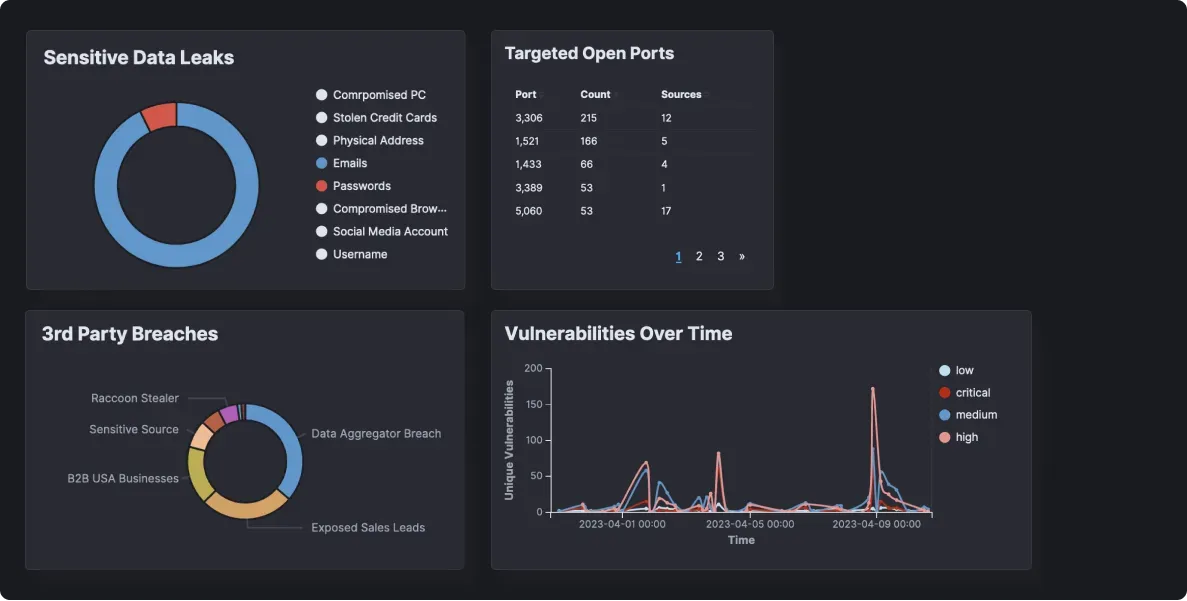

Integrated Attack Surface Management
Use our attack surface management solution to get a real-time view into any vulnerabilities, weaknesses, exposures, disclosures, insecure third parties and other anomalies in your Internet-facing services.
Integrated Attack Surface Management
Use our attack surface management solution to get a real-time view into any vulnerabilities, weaknesses, exposures, disclosures, insecure third parties and other anomalies in your Internet-facing services.

See Who is Targeting You and React Quickly
Prevent data breaches, discover security risks proactively and protect your data.
Mitigate Risks Proactively
Identify and analyze any security issues in your external perimeter in real time. Take proactive steps to mitigate risks before they are exploited by threat actors.Minimize Your Exposures
See what services attract hackers’ interest and what is being targeted. Gain visibility and take action before the hackers have had time to research your business and perfect their attack methods.Improve Your Decision-Making
Elevate Your Cybersecurity Strategy to Stay Ahead of Emerging Threats. Prioritize Security Investments and Make Informed Decisions to Protect Your Systems and Data.
Fully Integrated With Your SecOps Technology Suite
Our Attack Surface Management is fully integrated with our cloud-based SIEM and other SecOps tools. We correlate findings with other data and provide context to report only on what truly matters for your business.
Fully Integrated With Your SecOps Technology Suite
Our Attack Surface Management is fully integrated with our cloud-based SIEM and other SecOps tools. We correlate findings with other data and provide context to report only on what truly matters for your business.
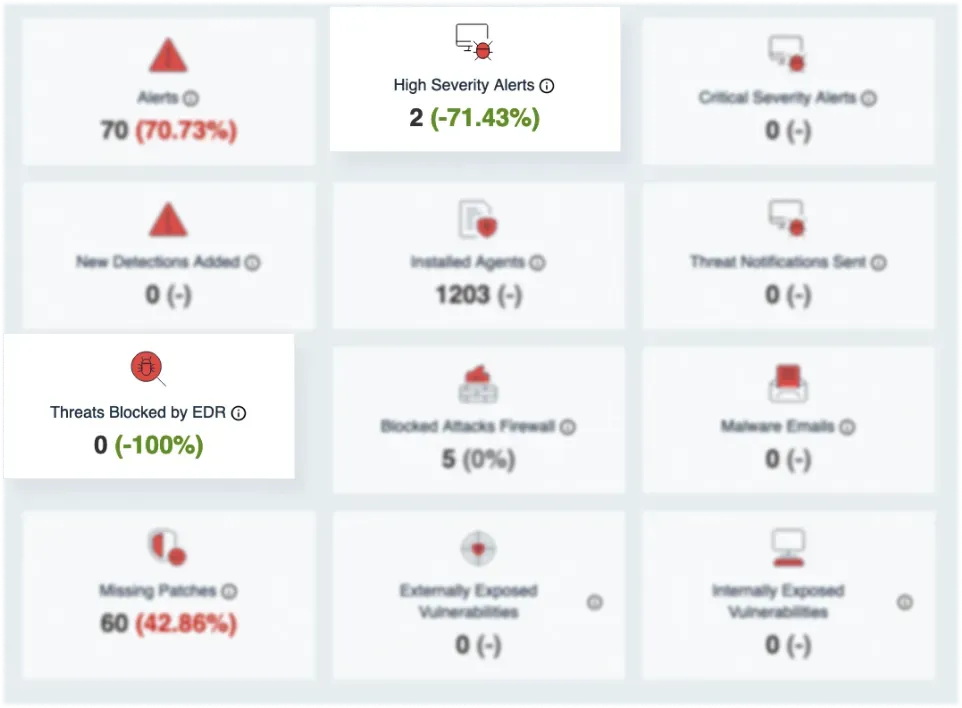
Fully Integrated With Your SecOps Technology Suite
Our Attack Surface Management is fully integrated with our cloud-based SIEM and other SecOps tools. We correlate findings with other data and provide context to report only on what truly matters for your business.
Fully Integrated With Your SecOps Technology Suite
Our Attack Surface Management is fully integrated with our cloud-based SIEM and other SecOps tools. We correlate findings with other data and provide context to report only on what truly matters for your business.

Our Areas of Concern Include:
- Insecure DNS domains and subdomains
- Risks in 3rd-party partner organizations
- Misconfigured SSL certificates
- Domains and websites impersonating your business
- External vulnerabilities, including web vulnerabilities
- Accidentally exposed services and portals
- Dark Web leaked credentials
- Risky websites, domains and IP addresses
- Insecure DNS domains and subdomains
- Risks in 3rd-party partner organizations
- Misconfigured SSL certificates
- Domains and websites impersonating your business
- External vulnerabilities, including web vulnerabilities
- Accidentally exposed services and portals
- Dark Web leaked credentials
- Risky websites, domains and IP addresses
Built-In Vulnerability Management
Our platform provides out-of-the box vulnerability management fully integrated into your SecOps suite.
Detect vulnerabilities in real time, and see what presents a real risk to your organization.
Built-In Vulnerability Management
Our platform provides out-of-the box vulnerability management fully integrated into your SecOps suite.
Detect vulnerabilities in real time, and see what presents a real risk to your organization.
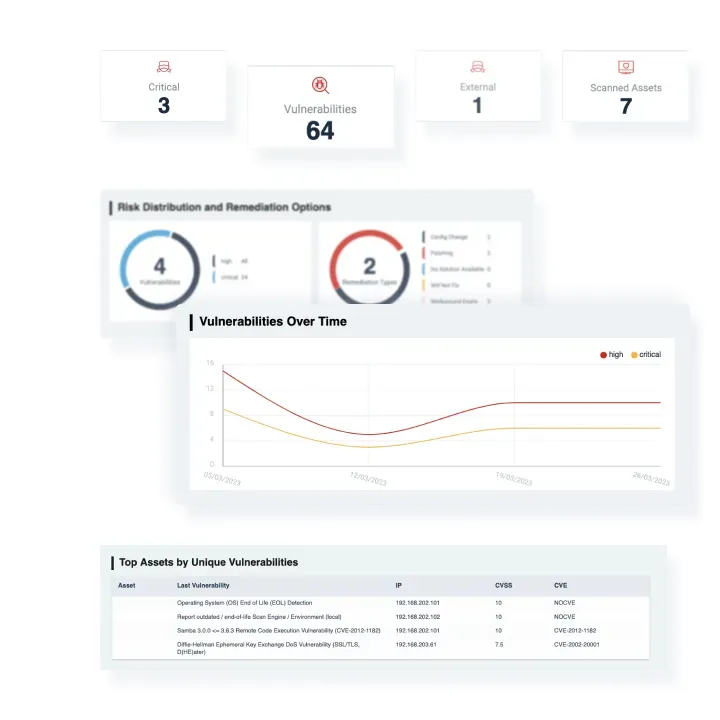
Built-In Vulnerability Management
Our platform provides out-of-the box vulnerability management fully integrated into your SecOps suite.
Detect vulnerabilities in real time, and see what presents a real risk to your organization.
Built-In Vulnerability Management
Our platform provides out-of-the box vulnerability management fully integrated into your SecOps suite.
Detect vulnerabilities in real time, and see what presents a real risk to your organization.

Dark Web Leaks
Discover any leaked documents, compromised user credentials, personal devices that may be controlled by hackers and any other Dark Web activity that may be associated with your business.
Dark Web Leaks
Discover any leaked documents, compromised user credentials, personal devices that may be controlled by hackers and any other Dark Web activity that may be associated with your business.
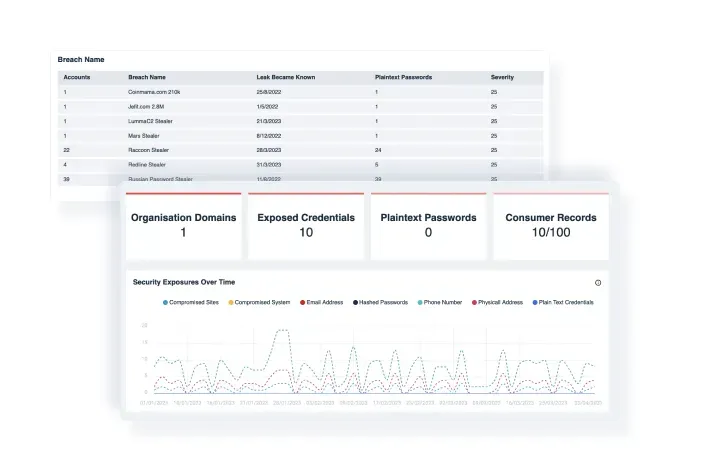
Dark Web Leaks
Discover any leaked documents, compromised user credentials, personal devices that may be controlled by hackers and any other Dark Web activity that may be associated with your business.
Dark Web Leaks
Discover any leaked documents, compromised user credentials, personal devices that may be controlled by hackers and any other Dark Web activity that may be associated with your business.

Exposed Services Discovery
With our platform, you can get visibility into unmanaged assets such as shadow IT, public cloud workloads, IoT devices, third-party hosted services and more.
Exposed Services Discovery
With our platform, you can get visibility into unmanaged assets such as shadow IT, public cloud workloads, IoT devices, third-party hosted services and more.
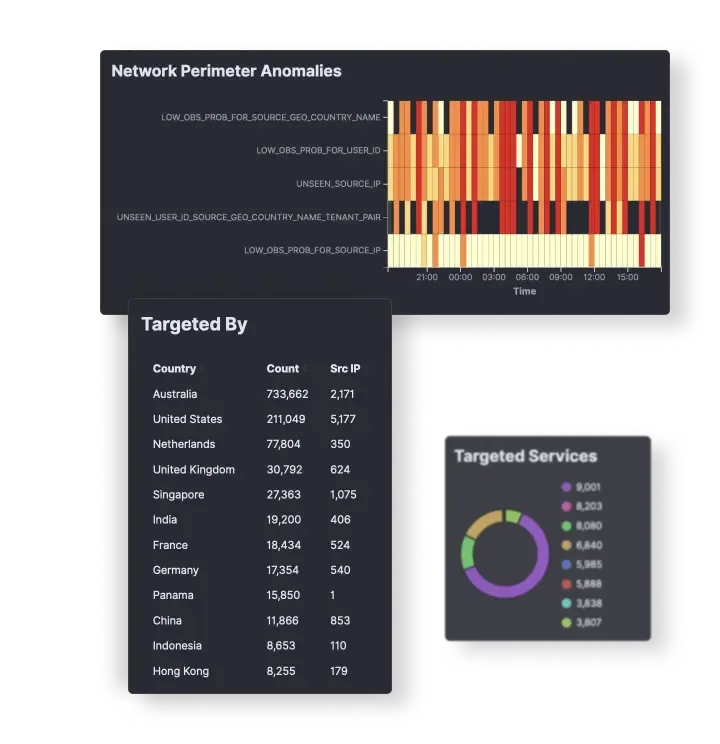
Exposed Services Discovery
With our platform, you can get visibility into unmanaged assets such as shadow IT, public cloud workloads, IoT devices, third-party hosted services and more.
Exposed Services Discovery
With our platform, you can get visibility into unmanaged assets such as shadow IT, public cloud workloads, IoT devices, third-party hosted services and more.

3rd Party Risk Management
Monitor the security posture of your 3rd parties and identify potential cyber risks that may arise from their exposures, compromised systems and poor security practices.
3rd Party Risk Management
Monitor the security posture of your 3rd parties and identify potential cyber risks that may arise from their exposures, compromised systems and poor security practices.
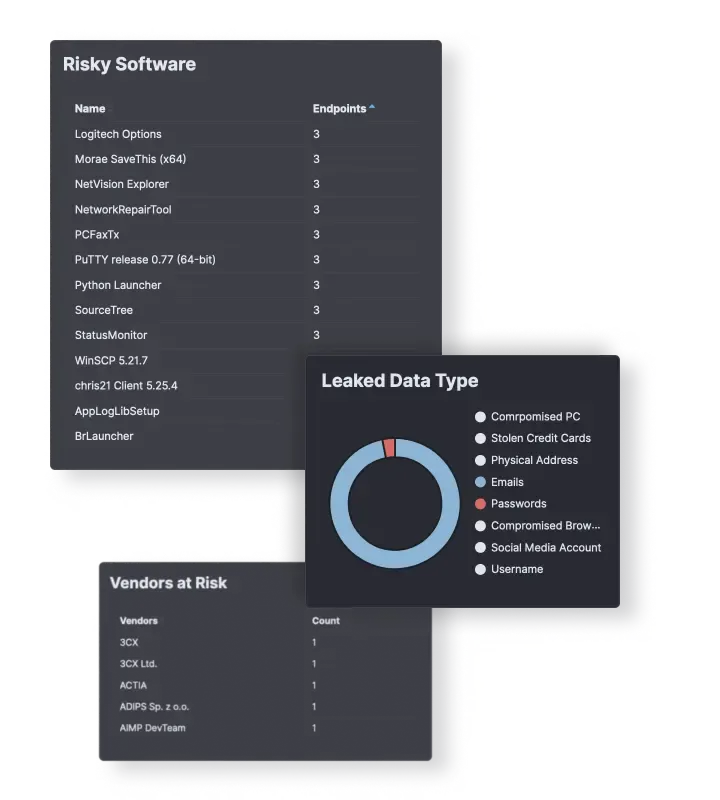
3rd Party Risk Management
Monitor the security posture of your 3rd parties and identify potential cyber risks that may arise from their exposures, compromised systems and poor security practices.
3rd Party Risk Management
Monitor the security posture of your 3rd parties and identify potential cyber risks that may arise from their exposures, compromised systems and poor security practices.
